- Generate Aes 256 Key Python Free
- Generate Aes 256 Key Python 3.5
- Generate Aes 256 Key Python 3
- Generate Aes 256 Key Python
Cryptography can be defined as the practice of hiding information and includes techniques for message-integrity checking, sender/receiver identity authentication, and digital signatures. The following are the four most common types of cryptography algorithms:
Next create the cipher using the key and the IV. We assume the key has been communicated using some other secure channel. Aes = AES.new (key, AES.MODECBC, iv) We also write the decrypted data to a “verification file”, so we can check the results of the encryption and decryption by comparing with the original file. The following are 30 code examples for showing how to use Crypto.PublicKey.RSA.generate.These examples are extracted from open source projects. You can vote up the ones you like or vote down the ones you don't like, and go to the original project or source file by following the links above each example. How can i generate random key for aes encryption. From Python 3.6 onwards you should use the secrets module for cryptograhically strong random. Python Create Aes Key Generate Aes Key Openssl Mar 12, 2020 Generating AES keys and password Use the OpenSSL command-line tool, which is included with InfoSphere® MDM, to generate AES 128-, 192-, or 256-bit keys. The madpwd3 utility is used to create the password.
- Hash functions: Also known as a one-way encryption, these have no key. A
hashfunction outputs a fixed-length hash value for plaintext input, and in theory, it's impossible to recover the length or content of the plaintext. One-waycryptographicfunctions are used in websites to store passwords in a manner they cannot be retrieved - Keyed hash functions: Used to build message-authentication codes (MACs); MACs are intended to prevent brute-force attacks. So, they are intentionally designed to be slow.
- Symmetric encryption: Output a ciphertext for some text input using a variable key, and you can decrypt the ciphertext using the same key. Algorithms that use the same key for both encryption and decryption are known as symmetric key algorithms.
- Public key algorithms: For public key algorithms, there are two different keys: one for encryption and the other for decryption. Users of this technology publish their public keywhile keeping their private key secret. This enables anyone to send them a message encrypted with the public key, which only the holder of the private key can decrypt. These algorithms are designed to make the search for the private key extremely difficult, even if the corresponding public key is known to an attacker.
For example, for hash functions, Python provides some modules, such as hashlib. The following script returns the md5 checksum of the file. The code for this article is available at here.
You can find the following code in the md5.py file in the hashlib folder in the repository:
The output of this script will be as follows:
Encrypting and decrypting information with pycrypto
When it comes to encrypting information with Python, one of the most reliable ones is the PyCrypto cryptographic library, which supports functions for block-encryption, flow-encryption, and hash-calculation.
The PyCrypto module provides all the necessary functions for implementing strong cryptography in a Python program, including both hash functions and encryption algorithms. For example, the block ciphers supported by pycrypto are:
Generate Aes 256 Key Python Free
- AES
- ARC2
- Blowfish
- CAST
- DES
- DES3
- IDEA
- RC5
In general, all these ciphers are used in the same way. You can use the Crypto.Cipher package to import a specific cipher type:
You can use the new method constructor to initialize the cipher:
With this method, only the key is mandatory, and you must take into account whether the type of encryption requires that it has a specific size. The possible modes are MODE_ECB, MODE_CBC, MODE_CFB, MODE_PGP, MODE_OFB, MODE_CTR, and MODE_OPENPGP.
If the MODE_CBC or MODE_CFB modes are used, the third parameter (Vector IV) must be initialized, which allows an initial value to be given to the cipher. Some ciphers may have optional parameters, such as AES, which can specify the block and key size with the block_size and key_size parameters.
In the same way as the hashlib, hash functions are also supported by pycrypto. The use of general hash functions with pycrypto is similar:
- Use the
Crypto.Hashpackage to import a specific hash type:from Crypto.Hash import [Hash Type] - Use the update method to set the datayouneedtoobtain the hash:
update('data') - Use the
hexdigest()method to generate the hash:hexdigest()
The following is the same example that you saw for obtaining the checksum of a file, in this case,you are using pycrypt instead of hashlib. You can find the following code in the hash.py file in the pycrypto folder:
To encrypt and decrypt data, you can use the encrypt and decrypt functions:
Encrypting and decrypting with the DES algorithm
DES is a block cipher, which means that the text to be encrypted is a multiple of eight, so you added spaces at the end of the text. When you decipher it, you remove it.
The following script encrypts a user and a password and, finally, simulating that it is the server that has received these credentials, decrypts, and displays this data.
You can find the following code in the Encrypt_decrypt_DES.py file in the pycrypto folder:
The program encrypts the data using DES, so the first thing it does is import the DES module and create an encoder with the following instruction:
The ‘mycipher’ parameter value is the encryption key. Once the cipher is created, encryption and decryption is quite simple.
Encrypting and decrypting with the AES algorithm
AES encryption needs a strong key. The stronger the key, the stronger your encryption. Your Initialization Vector needs to be 16 Bytes long. This will be generated using the random and string modules.
To use an encryption algorithm such as AES, you can import it from the Crypto.Cipher.AES package. As the PyCrypto block-level encryption API is very low level, it only accepts 16-, 24-, or 32-bytes-long keys for AES-128, AES-196, and AES-256, respectively.
Also, for AES encryption using pycrypto, you need to ensure that the data is a multiple of 16 bytes in length. Pad the buffer if it is not and include the size of the data at the beginning of the output, so the receiver can decrypt it properly.
You can find the following code in the Encrypt_decrypt_AES.py file in the pycrypto folder:
The output of the previous script will be as follows:
File encryption with AES
AES encryption requires that each block being written be a multiple of 16 bytes in size. So, you read, encrypt, and write the data in chunks. The chunk size is required to be a multiple of 16. The following script encrypts the file provided by the parameter. You can find the following code in the aes-file-encrypt.py file in the pycrypto folder:
The output of the previous script is a file called file.txt.encrypted, which contains the same content of the original file but the information is not legible. The previous script works in the way that first, you load all required modules and define the function to encrypt the file:

Also, you need to obtain your Initialization Vector. A 16-byte initialization vector is required, which is generated as follows:
Then, you can initialize the AES encryption method in the PyCrypto module:
File decryption with AES

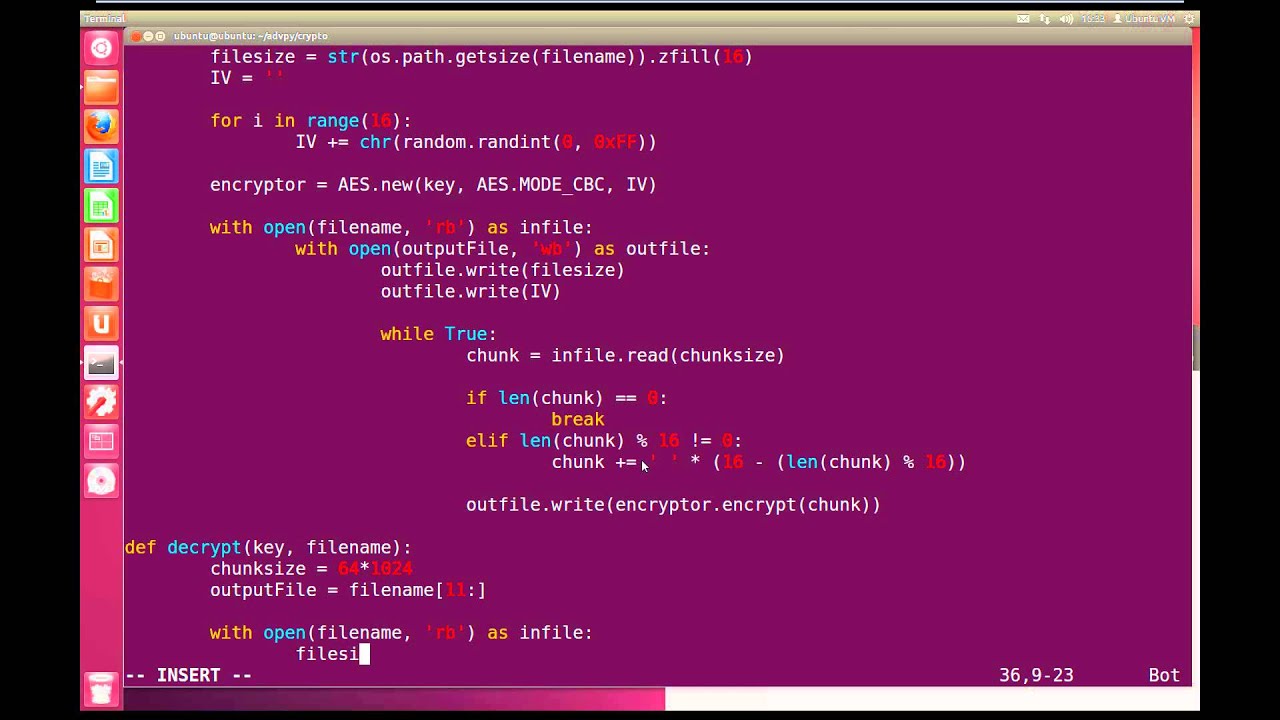
For decrypting, you need to reverse the preceding process using AES. You can find the following code in the aes-file-decrypt.py file in the pycrypto folder:
Encrypting and decrypting information with cryptography
Cryptography is a module more recent and it has better performance and security than pycrypto.
Introduction to cryptography
Cryptography is available in the pypi repository and you can install with the pip install cryptography command.
Cryptography includes both high-level and low-level interfaces to common cryptographic algorithms, such as symmetric ciphers, message digests, and key-derivation functions. For example, you can use symmetric encryption with the fernet package.
Symmetric encryption with the fernet package
Fernet is an implementation of symmetric encryption and guarantees that an encrypted message cannot be manipulated or read without the key. For generating the key, you can use the generate_key() method from the Fernet interface.
The following code is saved in the encrypt_decrypt.py file in the cryptography folder:
This is the output of the script:
Using passwords with the fernet package
It is possible to use passwords with Fernet. To do this, you need to run the password through a key-derivation function, such as PBKDF2HMAC. PBKDF2 (Password Based Key Derivation Function 2) is typically used for deriving a cryptographic key from a password.
In this example, you’ll this function to generate a key from a password and use that key to create the Fernet object for encrypting and decrypting data. In this case, the data to encrypt is a simple message string. You can use the verify() method, which checks whether deriving a new key from the supplied key generates the same key as the expected key.
Generate Aes 256 Key Python 3.5
You can find the following code in the encrypt_decrypt_kdf.py file in the cryptography folder:
This is the output of the script:
If you verify the key with the verify() method, and it checks that keys do not match during the process, it launches the cryptography.exceptions.InvalidKey exception:
Symmetric encryption with the ciphers package
The ciphers package from the cryptography module provides a class for symmetric encryption with the cryptography.hazmat.primitives.ciphers.Cipher class.
Cipher objects combine an algorithm, such as AES, with a mode, such as CBC or CTR. In the following script, you can see an example of encrypting and decrypting content with AES. You can find the code in the encrypt_decrypt_AES.py file in the cryptography folder:
This is the output of the previous script:
If you found this article interesting, you can explore José Manuel Ortega’s Mastering Python for Networking and Security to build a network and perform security operations. Mastering Python for Networking and Security will help you get the most out of the Python language to build secure and robust networks that are resilient to attacks.
In this section we shall explain how to implement elliptic-curve based public-key encryption / decryption (asymmetric encryption scheme based on ECC). This is non-trivial and usually involves a design of hybrid encryption scheme, involving ECC cryptography, ECDH key exchange and symmetric encryption algorithm.
Assume we have a ECC private-public key pair. We want to encrypt and decrypt data using these keys. By definition, asymmetric encryption works as follows: if we encrypt data by a private key, we will be able to decrypt the ciphertext later by the corresponding public key:
The above process can be directly applied for the RSA cryptosystem, but not for the ECC. The elliptic curve cryptography (ECC) does not directly provide encryption method. Instead, we can design a hybrid encryption scheme by using the ECDH (Elliptic Curve Diffie–Hellman) key exchange scheme to derive a shared secret key for symmetric data encryption and decryption.
This is how most hybrid encryption schemes works (the encryption process):
This is how most hybrid encryption schemes works (the decryption process):
Let's get into details how to design and implement an ECC-based hybrid encryption scheme.
ECC-Based Secret Key Derivation (using ECDH)
Assume we have a cryptographic elliptic curve over finite field, along with its generator point G. We can use the following two functions to calculate a shared a secret key for encryption and decryption (derived from the ECDH scheme):
- calculateEncryptionKey(pubKey) --> (sharedECCKey, ciphertextPubKey)
- Generate ciphertextPrivKey = new random private key.
- Calculate ciphertextPubKey = ciphertextPrivKey * G.
- Calculate the ECDH shared secret: sharedECCKey = pubKey * ciphertextPrivKey.
- Return both the sharedECCKey + ciphertextPubKey. Use the sharedECCKey for symmetric encryption. Use the randomly generated ciphertextPubKey to calculate the decryption key later.
- calculateDecryptionKey(privKey, ciphertextPubKey) --> sharedECCKey
- Calculate the the ECDH shared secret: sharedECCKey = ciphertextPubKey * privKey.
- Return the sharedECCKey and use it for the decryption.
The above calculations use the same math, like the ECDH algorithm (see the previous section). Recall that EC points have the following property:
- (a * G) * b = (b * G) * a
Now, assume that a = privKey, a * G = pubKey, b = ciphertextPrivKey, b * G = ciphertextPubKey.
The above equation takes the following form:
- pubKey * ciphertextPrivKey = ciphertextPubKey * privKey = sharedECCKey
This is what exactly the above two functions calculate, directly following the ECDH key agreement scheme. In the hybrid encryption schemes the encapsulated ciphertextPubKey is also known as 'ephemeral key', because it is used temporary, to derive the symmetric encryption key, using the ECDH key agreement scheme.
ECC-Based Secret Key Derivation - Example in Python
The below Python code uses the tinyec library to generate a ECC private-public key pair for the message recipient (based on the brainpoolP256r1 curve) and then derive a secret shared key (for encryption) and ephemeral ciphertext public key (for ECDH) from the recipient's public key and later derive the same secret shared key (for decryption) from the recipient's private key and the generated earlier ephemeral ciphertext public key:
Run the above code example: https://repl.it/@nakov/ECC-based-secret-key-derivation-in-Python.
The code is pretty simple and demonstrates that we can generate a pair { secret key + ciphertext public key } from given EC public key and later we can recover the same secret key from the pair { ciphertext public key + private key }. The above code produces output like this:
It is clear from the above output that the encryption key (derived from the public key) and the decryption key (derived from the corresponding private key) are the same. This is due to the above discussed property of the ECC: pubKey * ciphertextPrivKey = ciphertextPubKey * privKey. These keys will be used for data encryption and decryption in an integrated encryption scheme. The above output will be different if you run the code (due to the randomness used to generate ciphertextPrivKey, but the encryption and decryption keys will always be the same (the ECDH shared secret).
The above demonstrated mechanism for generating a shared ephemeral secret key, based on a ECC key pair, is an example of KEM (key encapsulation mechanism), based on the ECC and ECDH.
ECC-Based Hybrid Encryption / Decryption - Example in Python
Once we have the secret key, we can use it for symmetric data encryption, using a symmetric encryption scheme like AES-GCM or ChaCha20-Poly1305. Let's implement a fully-functional asymmetric ECC encryption and decryption hybrid scheme. It will be based on the brainpoolP256r1 curve and the AES-256-GCM authenticated symmetric cipher.
We shall use the tinyec and pycryptodome Python libraries respectively for ECC calculations and for the AES cipher:
Let's examine this full ECC + AES hybrid encryption example:
Run the above code example: https://repl.it/@nakov/ECC-based-hybrid-encryption-decryption-in-Python.
The above example starts from generating an ECC public + private key pair for the message recipient: pubKey + privKey, using the tinyec library. These keys will be used to encrypt the message msg through the hybrid encryption scheme (asymmetric ECC + symmetric AES) and to decrypt is later back to its original form.
Next, we encryptmsg by using the pubKey and we obtain as a result the following set of output: { ciphertext, nonce, authTag, ciphertextPubKey }. The ciphertext is obtained by the symmetric AES-GCM encryption, along with the nonce (random AES initialization vector) and authTag (the MAC code of the encrypted text, obtained by the GCM block mode). Additionally, we obtain a randomly generated ephemeral public key ciphertextPubKey, which will be encapsulated in the encrypted message and will be used to recover the AES symmetric key during the decryption (using the ECDH key agreement scheme, as it was show before).
To decrypt the encrypted message, we use the data produced during the encryption { ciphertext, nonce, authTag, ciphertextPubKey }, along with the decryption privateKey. The result is the decrypted plaintext message. We use authenticated encryption (GCM block mode), so if the decryption key or some other parameter is incorrect, the decryption will fail with an exception.
Generate Aes 256 Key Python 3
Internally, the encrypt_ECC(msg, pubKey) function first generates an ephemeral ECC key-pair for the ciphertext and calculates the symmetric encryption shared ECC key sharedECCKey = ciphertextPrivKey * pubKey. This key is an EC point, so it is then transformed to 256-bit AES secret key (integer) though hashing the point's x and y coordinates. Finally, the AES-256-GCM cipher (from pycryptodome) encrypts the message by the 256-bit shared secret key secretKey and produces as outputciphertext + nonce + authTag.
The decrypt_ECC(encryptedMsg{ciphertext, nonce, authTag, ciphertextPubKey}, privKey) function internally first calculates the symmetric encryption shared ECC key sharedECCKey = privKey * ciphertextPubKey. It is an EC point, so it should be first transformed to 256-bit AES secret key though hashing the point's x and y coordinates. Then the AES-256-GCM cipher is used to decrypt the ciphertext + nonce + authTag by the 256-bit shared secret key secretKey. The produced output is the original plaintext message (or an exception in case of incorrect decryption key or unmatching authTag).
The output from the above code looks like this:
Generate Aes 256 Key Python
Enjoy the above example, play with it, try to understand how exactly it works, try to change the underlying ECC curve, try to change the symmetric encryption algorithm, try to decrypt the ciphertext with wrong private key.