With Multi-Factor Authentication (also known as MFA or 2-Step Verification), you add an extra layer of security to your account.
After you set it up, you’ll sign in to your account in two steps using:
- Something you know (your password)
- Something you have (like your phone)
Important: If any sites prompt you to use 'Google Authenticator' for Multi-Factor Authentication (also known as MFA, 2-Step Verification, or 2FA), note that you can always substitute the Authy app instead. Although they work in similar ways, Authy is more feature-rich and allows for multi-device syncing, secure cloud-based backups, and easier account recovery should you change or lose your phone or device. More information on the features of Authy is available.
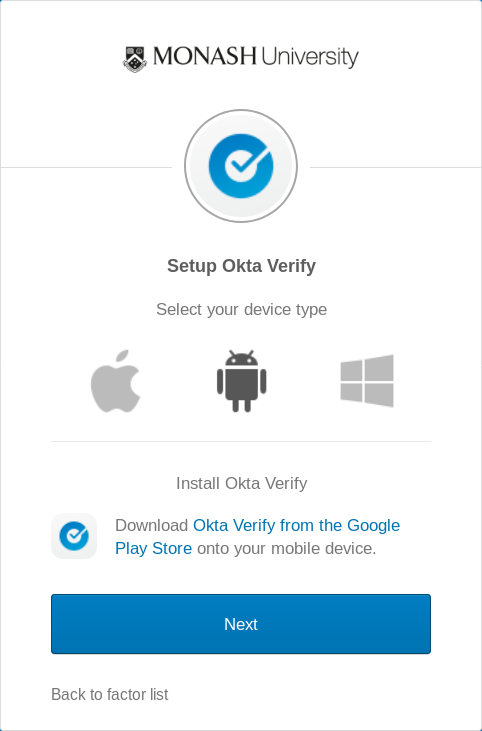
Okta Verify: Requires MobileIron; Doesn't require you to enter any codes or numbers. Allows you to verify your identity by an app on your mobile device instead of SMS text or voice call. Is available for iOS and Android devices. Can only be linked to one device at a time. Okta Verify (MacOS) Third Party Licenses and Notices OKTA - CONFIDENTIAL 020821 OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. JOSESwift Version (if any): 1.8.1 Brief Description: A framework for the JOSE standards JWS, JWE, and JWK written in Swift. License: Apache 2.0. 11 Download the Okta Verify app on your mobile device from the Apple AppStore or Google Play Store. Once you have downloaded the Okta Verify app, click Next. 12 Open Okta Verify on your mobile device and tap Add Account. 13 Using your mobile device, scan the barcode on screen.
To setup Multi-Factor Authentication (MFA) for Okta with Authy, follow these steps.
Okta Verify supports multifactor authentication with the Okta service Try Okta Free Trial Okta Verified The integration was either created by Okta or by Okta community users and then tested and verified by Okta.
Authy is a bit more technical to setup than Google Authenticator, but can be a significant help if you have multiple devices (phones, laptops, tablets), or if you need to change devices.
- On your computer, navigate to a website or service that requires Multi-Factor Authentication (MFA), such as https://checkmyokta.com/.
- Enter your username and password. Click the Sign In button.
- When presented with a prompt to set up Multi-Factor Authentication (MFA), click 'Setup' under the SMS Authentication option first. This is helpful if you lose, break, or replace your phone.
- Type in a phone number where you can receive SMS messages (text messages) and click 'Send code'.
- Check your mobile device. Enter the 6-digit code that was texted to you and click 'Verify'.
- Click 'Setup' under the Google Authenticator option.
Remember that when any site prompts you to use 'Google Authenticator' for Multi-Factor Authentication (MFA), you will be using the Authy app instead. - If you will be using an iPhone as your secondary device to help you get logged in, select iPhone. Otherwise, selectAndroid.
If you're not sure which option to choose, select Android. If you don't already have it installed, pause here and install the Authy app on your mobile device (instead of Google Authenticator). Links to the iOS App Store (for Apple products), Google Play Store (for Android and Samsung devices), Windows or Mac, and Linux are available. The YouTube video at https://youtu.be/EBdPzv75i3A?t=82 is a quick walk-through of how to set up Authy.
Open the Authy app on your mobile device.
In Authy, enter your phone number and your email address to create your Authy account.
Receive via SMS (text) message the registration code (or obtain it by phone call) and enter it into Authy to verify your new Authy account.
- In Authy, click Add Account.
- On iOS (iPhone), click the red + sign at the bottom of the screen in Authy to add a new MFA account for Okta.
- On Android & Samsung devices, tap the '…' icon in the upper right corner to open the menu, and select the Add Account option.
- On the Authy Desktop app, click the + (plus) sign in the upper right corner.
- Create a Authy Backups Password when prompted.
Use your mobile device to scan the QR Code displayed by Okta, then click Next.
In Authy, feel free to choose a new icon and rename the MFA token name for Okta.com: givename.surname@cru.org, if you like. Something like 'Okta' should be sufficient.
- Authy needs no internet connection to generate a time-based code, but it does require an accurate time on your mobile device. The Authy app will generate a 6-digit, time-based code on your mobile device.
Enter the 6-digit code that was generated by Authy into Okta and click Verify.
- If all went well, you are now setup to use Multi-Factor Authentication and should be signed into the website or service you were attempting to access!
You will want to add a secondary device to access Authy. This device will serve as a backup in case you lose access to your primary device. The 2nd device can be either a mobile device or the Authy desktop application. In the case that you do not have a 2nd device, please make sure to keep your phone number updated within the Authy application and follow the instructions below for Disable Multi-device.
Once you have Authy installed on the 2nd device do the following:
Authy Desktop - Additional Device
- Enable Multi-Device on one of your devices that already has Authy configured. (see below)
- Open Authy Desktop on the new device.
- Enter mobile phone number used during the initial setup.
- Click Next.
- Click Existing Device to indicate verification method.
- Switch to the Initial Authy Device.
- There should be a prompt asking for the new device to be authorized. Type OK and then click or tap OK.
Authy on Android or iOS - Additional Device
- Open Authy on the new device.
- Enter mobile phone number used during the initial setup.
- Touch or click OK.
- Touch or click ADD NEW DEVICE.
- Enter a name for the device and touch or click ADD DEVICE.
- Switch to the Initial Authy Device.
- There should be a prompt asking for the new device to be authorized. Type OK and then click or tap OK.
You may need to click on an existing two factor token listed and enter the backup password you provided during the initial setup of Authy to access the tokens from this new device.
Okta Verify App Mac Computer
Disable/Enable Multi-device (recommended, not required)
This keeps people from being able to hack into your Authy - even if they get your Authy password
Open Authy on any of your devices and perform the following instructions.
Authy Desktop
- Click Settings on the main screen.
- Click Devices.
- Click Disable next to Multi-device (or Enable if you want to add new devices))
Authy on Android or iOS
- Tap Settings under the mobile app menu.
- Tap Devices.
- Slide the switch to disable setting for “Allow multi-device” (or Enable if you want to add new devices))
This will prevent the adding of new devices which could be added by hijacking your phone number.
You will must Enable Multi-Device before you add a new device. Disable Multi-Device once you’ve added the new device(s).
Okta Single Sign On (SSO) FAQs

What is Okta, SSO, and MFA?
You may hear different terminology when discussing how to access WSU’s network resources. To clarify the differences:
Okta is the name of the vendor who supplies WSU’s current SSO login process and MFA (Multi-Factor Authentication) service.
SSO is an acronym for “single sign on,” which is the name for the authentication or log in process that allows WSU users to access most university software applications with a single set of login credentials.
MFA or Multi-Factor Authentication (sometimes referred to as “two-factor” or “extra verification”) is WSU’s added security authentication step that requires a user to enter their network ID (NID) and password, followed by a code received through one of the following options:
- Authentication app on a mobile device (Okta Verify or Google Authenticator)
- Voice call
- USB Key
- Text message (SMS)
Users who need to access WSU resources will receive an invitation to set up their WSU NID (network ID) or friend ID (FID) and password, as well as MFA preferences, at account.wsu.edu.
- Users will receive reminders to reset their account password every 6 months
- For assistance creating an Okta-compliant password, google ‘password generator’ and find a number of online sites ready to help.
- Already have your WSU password, but need to visit the WSU password management site? Visit account.wsu.edu anytime.

Departments Requesting WSU Single Sign On Functionality
Departments who wish to request WSU SSO for their applications should contact ITS. Please submit a request through the self-help portal at crimsonservicedesk.wsu.edu with your name, phone number, application name, and application description. After submitting your service desk ticket, a member of ITS will reach out to you with more information and instructions on how to begin testing for on-boarding your application(s).
Current List of Applications Now Using MFA
There are approximately ninety applications currently using Okta that require MFA. Please reach out to your department’s system administrators or technical support staff for information on your local applications. The list of top university-wide applications can be found below.
Top Applications Currently Requiring MFA:
- Office 365
- myWSU
- Adobe Creative Cloud
- Zoom video conferencing
- Canvas
- Blackboard
- WSU Mobile
- Matlab
- eXplorance Blue
—and more.
| WSU Apps Using Okta Security |
|---|
| ad.wsu.edu |
| Adobe Creative Cloud |
| Amazon Web Services |
| Amazon Web Services SPO |
| AOI ALN |
| AOI Apps |
| AOI eLearning |
| AOI oidc-test |
| ASIS - Umbraco - SA CMS Dev |
| ASIS-Siteimprove |
| ASIS-SSO_Dev |
| ASIS-SSO_Prod |
| Blackboard Learn |
| Blackboard Stage |
| Budget Planning System |
| CAHNRS Authenticate OAuth |
| CampusM |
| Canvas |
| Canvas - TEST |
| CCB EduSourced |
| CCB Suitable |
| Cloudways |
| COE AWS AppStream |
| Comevo Online Orientation |
| CVM eSuggestion Box |
| CVM eSuggestion Box - Test |
| CVM Group Manager |
| CVM Preceptors |
| CVM TRC |
| CVM Veterinary Teaching Hospital Community Practice Calendar |
| CVM Veterinary Teaching Hospital Computer Survey/Audit |
| CVM Veterinary Teaching Hospital Faxing Center |
| CVM Veterinary Teaching Hospital Item Database |
| CVM Veterinary Teaching Hospital Medical Record Tracking |
| CVM Veterinary Teaching Hospital Patient Safety Report |
| CVM Veterinary Teaching Hospital Scrub Tracking |
| CVM VTH Online Payments |
| DocuSign |
| E.Flo Colleagues |
| E.Flo Colleagues Dev |
| EIT TWILIO FLEX |
| ESFCOM Admissions |
| ESG Github |
| ESG IBM Cloud |
| ESG Jenkins |
| EYP LMS |
| FAIS - AIMS Test |
| FAIS Signage TEST |
| Flex Cougar Connector |
| FLEX Helpdesk |
| FLEX SFS |
| FLEX Vancouver |
| G Suite |
| iGrad |
| iGrad Test |
| Inteum |
| Inteum DEV |
| ITS Global Protect Test VPN |
| ITS-Forms |
| ITS-FormsSSO |
| Juristat |
| Legacy Apps |
| Meraki CIT Test Lab SAML |
| Meraki Everett SAML |
| Meraki Extension Network |
| Meraki FullAdmin TEST |
| MFA Test |
| MyWSU |
| NanoVest |
| Oracle Cloud Infrastructure |
| PnC - Web Portal |
| ResLife - Qualtrics 360 |
| Salesforce-OC |
| Settings |
| Shibboleth SP |
| Slate Enrollment CRM |
| Slate Test |
| SplunkES |
| TC FreePBX |
| TC PaperCut |
| TC Persona Campus SAML |
| Title IX Training |
| UREC-Attic-Dev |
| VAN Apporto |
| VAN ENCS AutoLab |
| VAN ENCS AutoLab-Dev |
| WADDL Portal Admin |
| WADDL Portal Admin Test |
| webSSO |
| Zoom |
| ZoomRoom Web App |
Okta Verify App Mac Download
| Adobe Creative Cloud | ESG Jenkins |
| Amazon Web Services | EYP LMS |
| AOI ALN | ITS Global Protect Test VPN |
| AOI Apps | Legacy Apps (Mainframe, WSU Notices) |
| AOI eLearning | MFA Test |
| ASIS-SSO | MyWSU |
| Blackboard Learn | Oracle Cloud Infrastructure |
| Budget Planning System | ResLife - Qualtrics 360 |
| CAHNRS Authenticate | Settings |
| CampusM | Slate Enrollment CRM |
| Canvas | TC FreePBX |
| CCB EduSourced | TC PaperCut |
| CCB Suitable | TC Persona Campus SAML |
| CVM eSuggestion Box | Title IX Training |
| CVM Preceptors | UREC-Attic-Dev |
| CVM Veterinary Teaching Hospital Community Practice Calendar | VAN ENCS AutoLab-Dev |
| CVM Veterinary Teaching Hospital Faxing Center | WADDL Portal Admin |
| CVM Veterinary Teaching Hospital Item Database | webSSO (Ucomm) |
| CVM Veterinary Teaching Hospital Medical Record Tracking | Zoom |
| CVM Veterinary Teaching Hospital Patient Safety Report | |
| EIT TWILIO FLEX | |
| ESFCOM Admissions | |
| ESG Github | |
| ESG IBM Cloud |